Policy Management Walk Through¶
In this tutorial / walk through, we'll step you through an example IAM scenario. We're going to create a team as shown in the figure below which represents the IAM resources we'll be creating. We'll be creating VECTR environment resources along with groups, policies, and users. A group is a collection of users who have similar responsibilities. Each group can have multiple users and each user can be in more than one group, although the figure doesn't illustrate that. You can't put groups inside other groups. You use policies to grant permissions to groups.
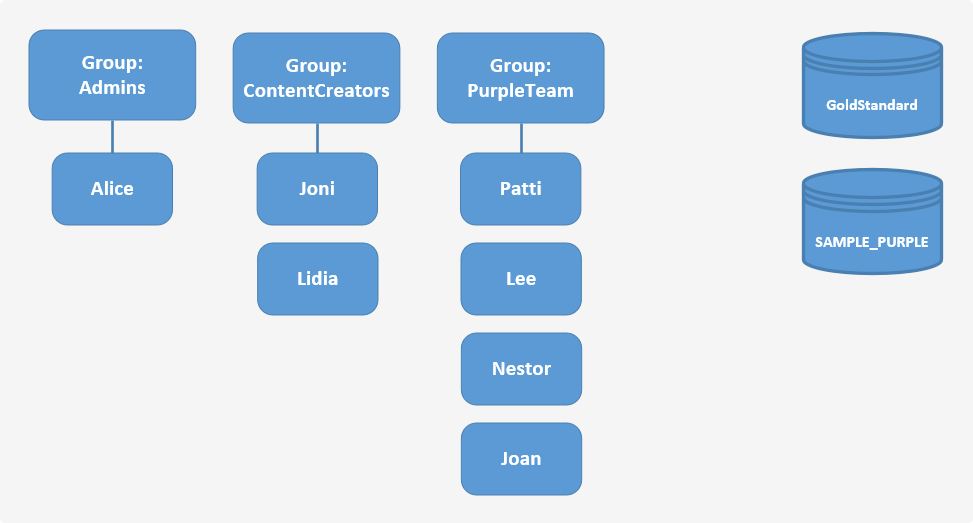
Permission Matrix¶
The following table outlines the resource permission matrix. We'll use this matrix to define our policies and determine the appropriate permission for each group.
| Group | Resource | Permission |
|---|---|---|
| Admins | GoldStandard | read, write |
| Admins | SAMPLE_PURPLE | read, write |
| ContentCreators | GoldStandard | read, write |
| ContentCreators | SAMPLE_PURPLE | read, write |
| PurpleTeam | GoldStandard | read |
| PurpleTeam | SAMPLE_PURPLE | read, write |
At first glance, it may seem that we need to create three policies to provide the permissions that we need. Let's go over some default policies that ship with VECTR to see how we can utilize them for our use case:
- Users belonging to the
Adminsbuilt-in group already has full access to all resources in VECTR. - We can use the
GoldStandardFullAccessbuilt-in policy to give theContentCreatorsgroupreadandwriteaccess toGoldStandard. - Adding all of our users to the
BasicAccessbuilt-in group will providereadaccess toGoldStandard.
With this information on hand, we only need to create a single policy that provides read and write access on our SAMPLE_PURPLE environment. We'll cover how to do this as well as steps to perform the rest of our tasks in the sections below.
Overview¶
To goal of this tutorial is to create the groups, policies, and users to implement our example scenario and provide the permissions which we've outlined in the permission matrix above. In our example, the team has a single administrator, content creators who are responsible for creating our purple team playbook, and a group of people that will be conducting the purple team assessment.
Everyone needs some level of access to the GoldStandard library which contains template data for the purple team assessment. Additionally, everyone needs to be able to read and write to the environment (SAMPLE_PURPLE) that will be used to record the assessment.
Now that we know what permissions and environments we need to have access to, let's review the list of tasks to achieve our goal:
- Create a user and add that user to the
Adminsgroup - Using this administrator user:
- Create the sample
SAMPLE_PURPLEenvironment - Create policies
- Create groups and assign policies to the group
- Create users and assign them to groups
- Create the sample
Create an Administrator User¶
As a best practice, do not use the VECTR root user for your day-to-day tasks. Instead, create a new user for each person that requires administrative permissions.
- Log into VECTR as the root user.
- From top navigation, choose the Configuration cog in the top right VECTR Configuration and select Asset Management.
- Click on the Users tab.
- Click on Create New User.
- Provide the following:
- Full Name. This can be a real name or a "friendly/display name".
- Username. This is the sign-in name for the application. Username can contain alphanumeric, plus (
+), period (.), at sign (@), underscore (_), and hyphen (-) characters. - Password. Provide a password of your choosing. To toggle password visibility, click the icon.
- Click Next.
- Click on the Add to Group tab. Select
Admins. - Click Save.
- Log out and then log back in using your new user account.
Note
Each subsequent section below will assume that you are already logged into VECTR with your administrator user.
Create an Environment¶
We'll create a VECTR environment that will be used to record our purple team assessments. For an overview on what an environment is, head over to Important Concepts.
- Click on the Environments dropdown in the VECTR toolbar.
- Click Select Active Environment.
- Click on the icon.
- Enter
SAMPLE_PURPLEas the environment name. - Click Submit.
- Select
SAMPLE_PURPLEif it's not already selected. - Click Done.
Create Policies¶
Using the permission matrix defined in the table above, we'll create a set of policies that will enforce the permissions we've defined.
Create a Policy that Allows read and write access to SAMPLE_PURPLE¶
- From top navigation, choose the Configuration cog in the top right VECTR Configuration and select Asset Management.
- Click on the Policies tab.
- Click on Create New Policy.
- Select User or Group Based.
- Click Next.
- Enter policy information:
- Policy Name: PurpleTeamEditorPolicy
- Description: Policy that allows read and write access for purple team related environments.
- Click Next.
- Create a rule for your policy:
- Resources. Select
SAMPLE_PURPLE. - Actions. Select
readandwrite.
- Resources. Select
- Click Save.
Create Groups¶
Again, we'll refer to the permission matrix to figure out the policies that our groups will need. As a best practice, you want to assign the least number of permissions to a group to provide the necessary access to the specific group.
Create the ContentCreators Group¶
Based on our permission matrix, the only unique permission that this group needs is the ability to read and write to GoldStandard. The other permissions can be given through other groups and/or policies. This should make a little more sense when you get to creating the users.
- From top navigation, choose the Configuration cog in the top right VECTR Configuration and select Asset Management.
- Click on the Groups tab.
- Click Create New Group.
- Provide the following:
- Group Name: ContentCreators
- Description: Group for our purple team content creators.
- Click Next.
- We'll skip this step as we don't have any users yet.
- Click Next.
- Select the following policies:
GoldStandardFullAccess
- Click Save.
Create the PurpleTeam Group¶
When you are creating groups that will give access to specific environments, it is best practice to add the ListDatabase and TagManagement built-in policies as these provide access to common actions performed on a database. Specifically, the ListDatabase and TagManagement policies provide the ability for users to list databases in which they have access to, and the ability to create and edit tags, respectively.
- From top navigation, choose the Configuration cog in the top right VECTR Configuration and select Asset Management.
- Click on the Groups tab.
- Click Create New Group.
- Provide the following:
- Group Name: PurpleTeam
- Description: Group for those who will be conducting purple team assessments.
- Click Next.
- We'll skip this step as we don't have any users yet.
- Click Next.
- Select the following policies:
ListDatabasesPurpleTeamEditorPolicyTagManagement
- Click Save.
Create Users¶
We'll first walk you through how to create a new user and then identify the specific groups each user should belong to.
How to Create a New User¶
Follow these steps for creating each of our example users:
- From top navigation, choose the Configuration cog in the top right VECTR Configuration and select Asset Management.
- Click on the Users tab.
- Click on Create New User.
- Enter a full name, username, and password. For the full name and username, use the name from our diagram. Enter any value for the password.
- Click Next.
- Click on the Add to Group tab. Select the groups based on the table mapping shown below.
- Click Save.
User and Group Mapping¶
| User | Groups |
|---|---|
| Joni | BasicAccess, ContentCreators, PurpleTeam |
| Lidia | BasicAccess, ContentCreators, PurpleTeam |
| Patti | BasicAccess, PurpleTeam |
| Lee | BasicAccess, PurpleTeam |
| Nestor | BasicAccess, PurpleTeam |
| Joan | BasicAccess, PurpleTeam |
Wrap Up¶
Now that you've walked through an example IAM scenario, you can use these same techniques to determine the permissions needed for each member of your team that uses VECTR. Remember that the built-in groups and policies provide many of the basic permissions needed to access VECTR, we recommend that you use these in your IAM implementations.