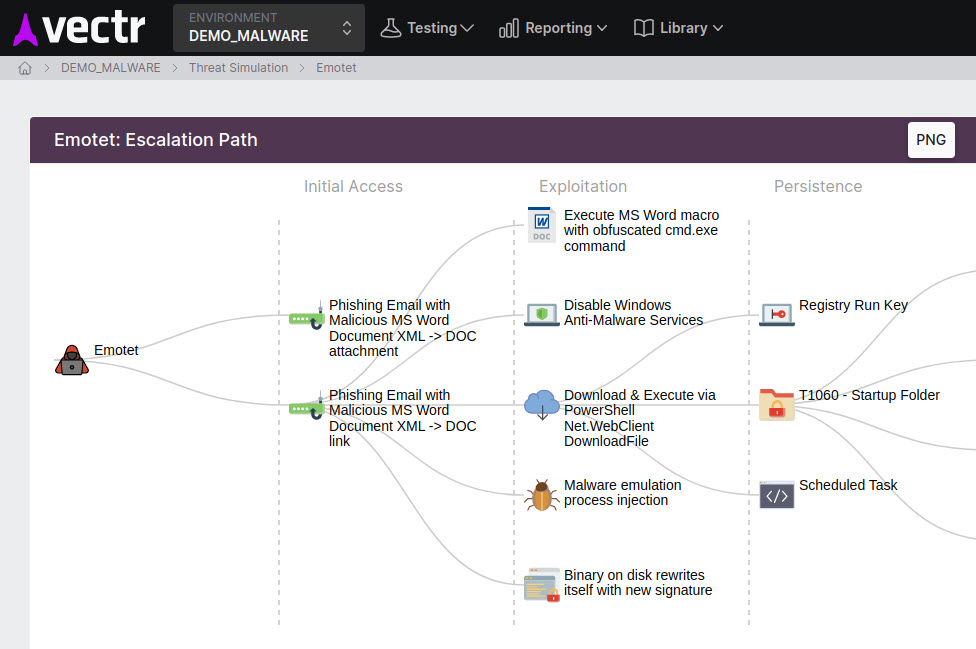
Terminology and Vocabulary¶
Kill Chains, Phases, Tactics, and Techniques¶
Initially, one of the most well-known frameworks for categorizing cyberattacks was the Lockheed Martin Cyber Kill Chain, first discussed in 2011. You will see references to Kill Chains and Phases in VECTR because of the popularity of this taxonomy.
MITRE Enterprise ATT&CK was created in 2013, but public awareness increased in 2017 and 2018 as the project published very useful cyber threat intelligence, web resources, and the intelligence sharing tool, Unfetter.
The Cyber Kill Chain is roughly equivalent to a MITRE ATT&CK Framework's depiction of all its Tactics like the complete list of Enterprise ATT&CK Tactics. Within the frameworks, a Kill Chain Phase is roughly equivalent to an ATT&CK Tactic.
MITRE to VECTR Terminology
Framework¶
Kill Chain - The MITRE Enterprise ATT&CK Framework or MITRE ATT&CK for Industrial Control Systems would be an example of a Kill Chain in VECTR. Non-MITRE examples would be the Unified Kill Chain or Lockheed Martin Cyber Kill Chain.
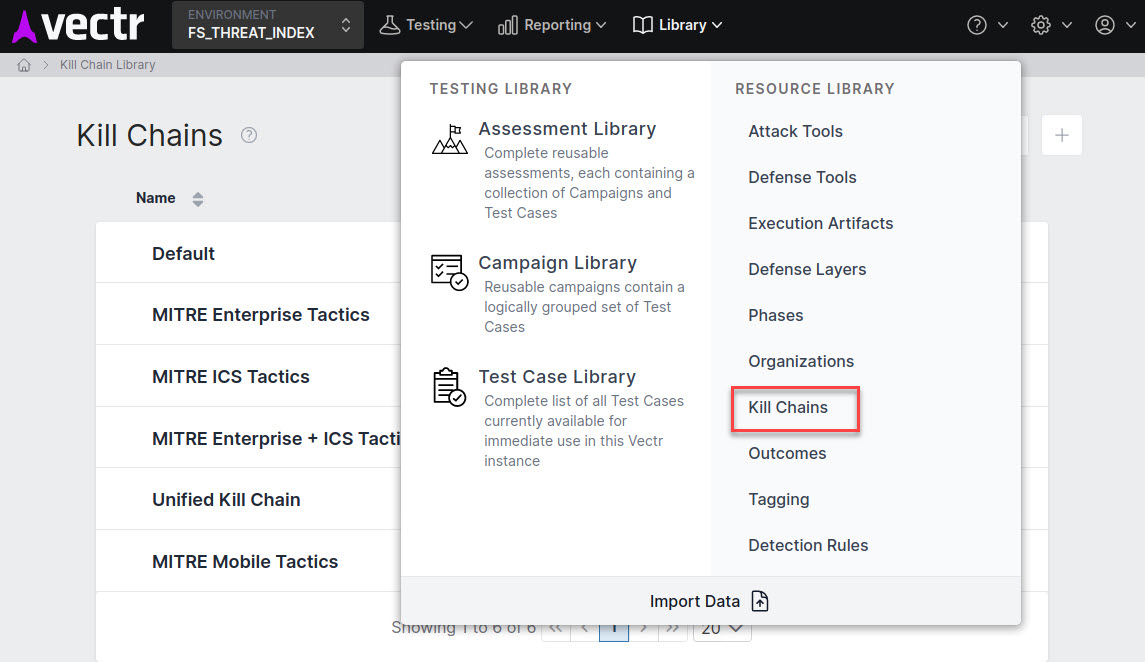
Tactic¶
Phase - A MITRE Enterprise ATT&CK Tactic is equivalent to a Phase in VECTR. Some examples of these are Discovery, Exploitation, and Execution.
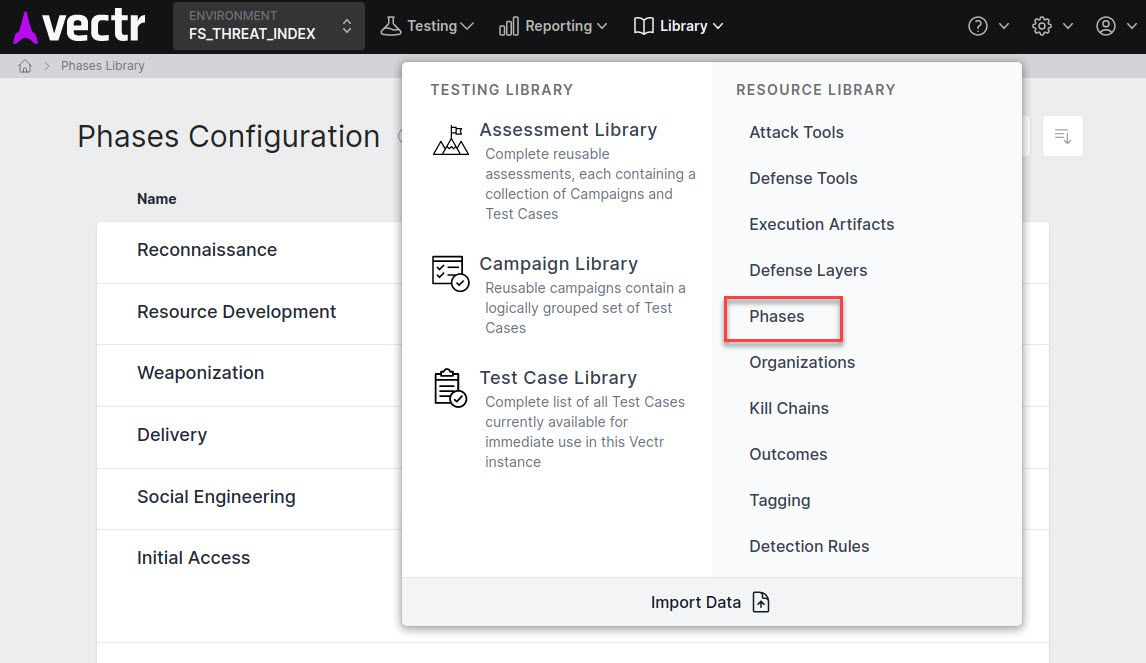
Technique and Sub-Technique¶
Technique or Method - A Technique or Sub-Technique in MITRE ATT&CK like T1053.005 - Scheduled Task is similarly called a Technique in VECTR.
Additionally, VECTR has a specific Mitre ID field that is filled out when selecting a Technique. Before the popularity of MITRE ATT&CK, VECTR referred to a Technique as a "Method" or "Attack Method." You may see this phrasing in older publications.
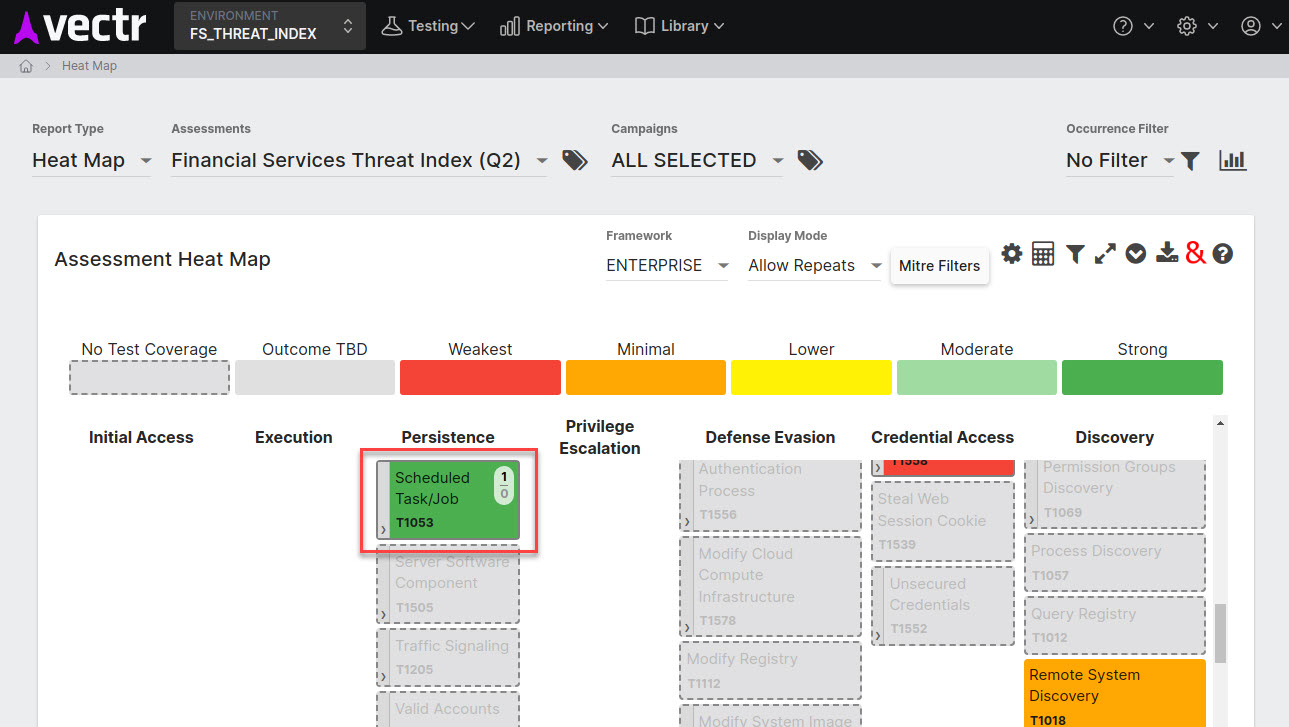
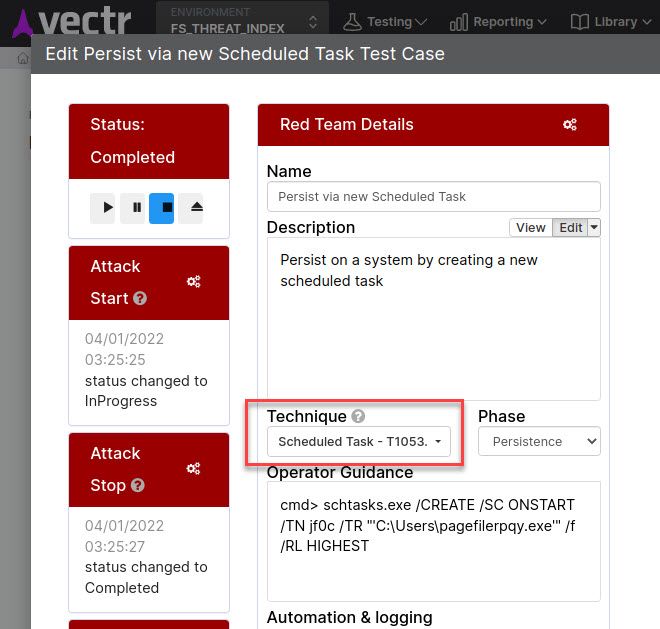
Procedure¶
Test Case, Variant, or Test Case Template - In some MITRE publications, specific instances of attack methods categorized by a Technique ID are described as Procedures. In VECTR, we record the Procedure in general as a Test Case Template.
The specific use of a Procedure, such as what you would do during the simulated attacks comprising a Purple Team, would be recorded in VECTR as a Test Case. Older publications may use the word "Variant" or phrase "Attack Variant" to describe this as well.
Adversary Emulation and Simulation¶
Purple Team exercises can focus on specific, common threats or can be designed to emulate adversaries or malware that may target an organization or industry.
Using Cyber Threat Intelligence to inform and plan Purple Team activities was colloquially referred to as "Risk-Based Assessment Planning" or "Industry-Specific Adversary Simulation". More recently, vocabulary such as "Threat-Informed Defense" is being evangelized by vendors and academic sources to cover these and other related activities.