Integrate with Microsoft Azure AD¶
This guide serves as a reference for configuring SSO with Microsoft Azure AD using the OpenID Connect protocol.
Attention
Your VECTR instance must be able to connect to the internet in order to set up and use SSO with Azure AD.
Prerequisites¶
Determine your VECTR callback URL¶
The callback URL will be your VECTR domain followed by /auth/login/callback. For example:
- VECTR domain:
sravectr.internal - VECTR callback URL will be:
https://sravectr.internal/auth/login/callback
You will need to enter your VECTR callback URL when registering VECTR in the Azure Portal.
Register VECTR in the Azure Portal¶
To register your app with Azure AD, see Microsoft's Quickstart: Register an application with the Microsoft identity platform.
Attention
If you have more than one Azure AD directory, make sure you are in the correct directory when you register VECTR.
During registration, configure the following settings:
| Option | Value |
|---|---|
| Redirect URI | Select a Redirect URI type of Web, and enter your callback URL: https://<VECTR_DOMAIN>/auth/login/callback. |
During this process, Microsoft generates an Application (client) ID for your application; you can find this on the app's Overview screen. Make note of this value.
Configure Client Secret¶
To create a client secret, see Microsoft's Quickstart: Register an application - Add Credentials.
Once generated, make note of this value.
Note
Make sure to record the expiration date; you will need to renew the key before that day to avoid a service interruption.
Add Permissions¶
To add permissions, see Microsoft's Quickstart: Configure a client application to access a web API - Add permissions to access Microsoft Graph.
You will need to configure permissions for the Microsoft Graph API.
While setting up your permissions, configure the following settings:
| Field | Description |
|---|---|
| Delegated permissions | Required |
OpenId permissions:
|
So VECTR can sign in users and read the signed in users' profile |
User:
|
So VECTR can sign in users and read the signed in users' profile |
Configure an Identity Provider in VECTR¶
-
Log into VECTR as an admin
-
Navigate to Configuration -> VECTR Configuration -> Access Management -> Identity Providers
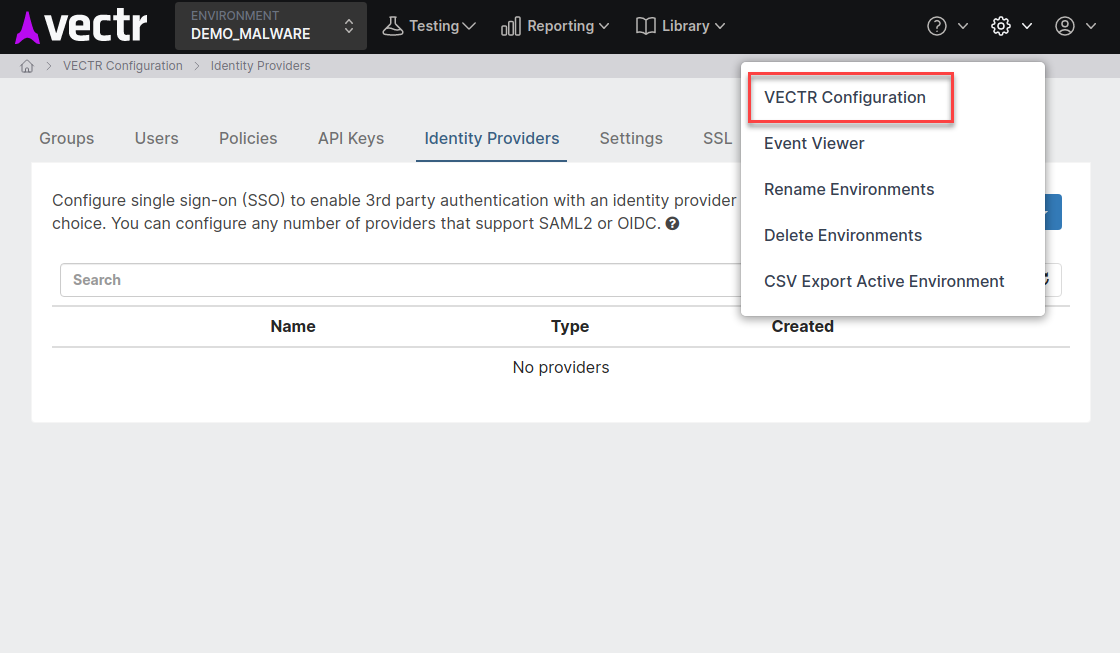
-
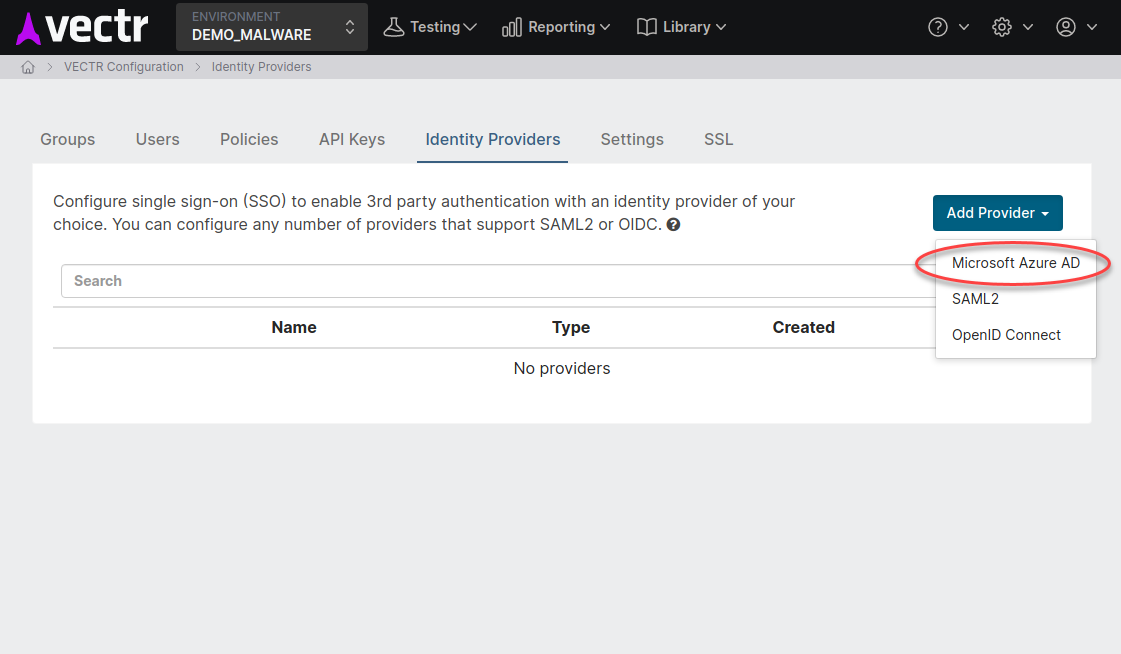
Click Add Provider -> Microsoft Azure AD
-
Enter the Identity Provider information, then click Next:
Field Description Required Display Name The name used to customize the login button on the login page. When set, the button will read "Log in with [Display Name]". YES Application ID The ID of your Azure AD application. This can be located in the application registration section of Azure AD. YES Tenant ID The ID of your Azure AD tenant. This can be located in the application registration section of Azure AD. YES Client Secret The client secret that you created when registering VECTR in Azure AD. YES Logo URL URL of an image to use to for the login button. When set, the button will display the image as a 20px by 20px square. NO 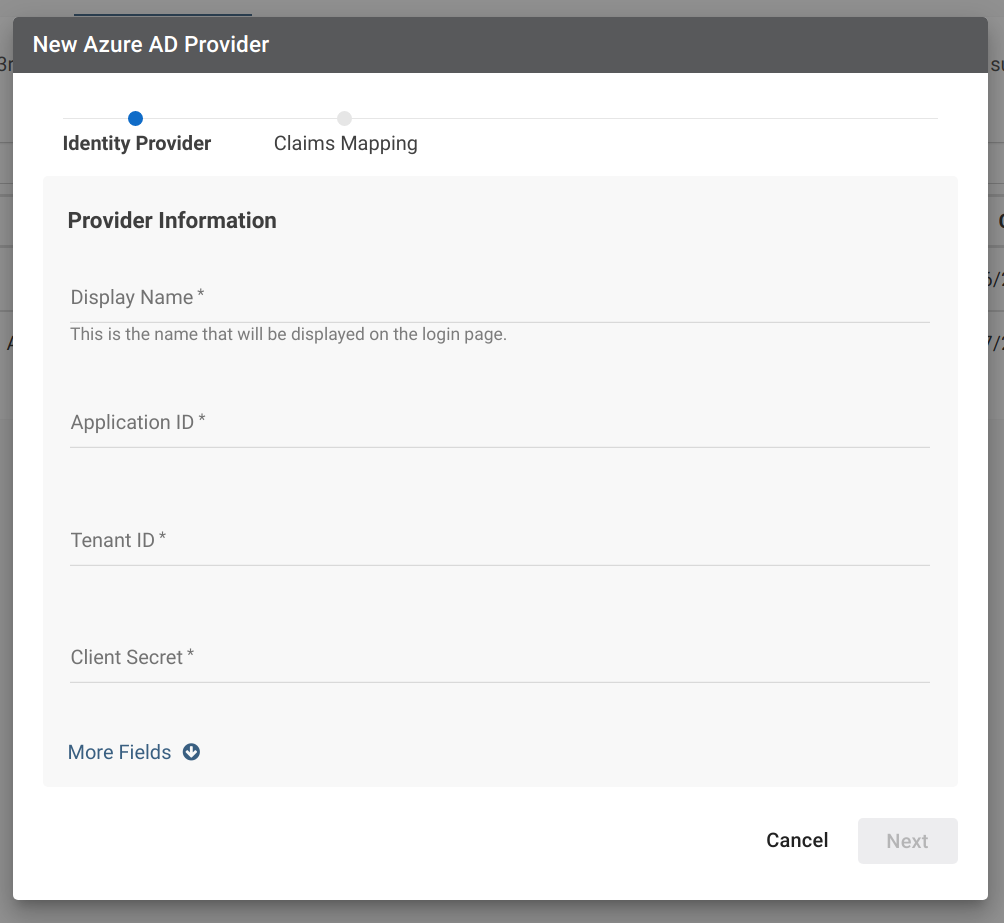
-
Claims mapping. You can generally use the default values provided. Click Save when you are done.
Attention
If you make changes to the claims mapping, be sure that the value mapping is configured in Azure AD as well.
-
Copy the information provided on the Configuration Info tab to your Azure AD application
Optional Step
This set is optional if you have already specified the callback URL when registering VECTR in the Azure Portal.
-
Click Done
Test the Connection¶
To test the integration, open a new Incognito window and go to your VECTR instance. You should see a new login method for Azure AD. Click on the button and follow the Azure AD authentication flow. After you have authenticated, you should see a screen requesting access to VECTR:
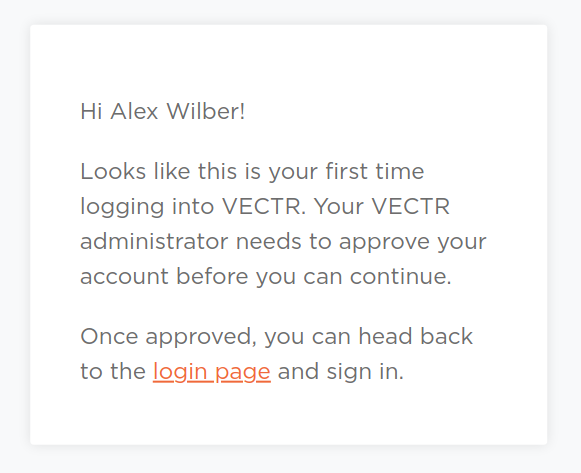
This is the access pending page that all SSO users will see the first time they authenticate with VECTR using Azure AD. To read more about managing SSO users, see the Managing SSO Users page.